IT networks are an indispensable part of today’s world. They enable all our devices to communicate with each other – without networks there would be no Internet, no telephone and no corporate IT. They connect the smartphone with wireless headphones as well as with the conversation partner on the other side of the world. Functioning networks are a cornerstone of our modern digital world. It is all the more important that communication between devices always functions smoothly.
This blogpost answers the following questions: What is a network made of? What types of networks are there? How do the components communicate with each other?
1 What is a network?
In information technology (IT), a network is an association of several computers or other devices such as smartphones or IP cameras that can communicate with each other, i.e. exchange data.
IT networks come in very different sizes and complexities. The simplest network is created when two devices are directly connected, for example when Bluetooth headphones are paired with a smartphone. The data exchanged in this case is the data stream, which contains the audio data.
When most people hear the term “network”, they first think of an interconnected group of several computers and servers, as is the case, for example, with an internal company network. In such a network, the computers are connected to at least one server which, among other things, provides data via network drives. This type of network is explained in more detail in Chapter 2.
Probably the best known and most complex network in the world is the Internet. It links countless smaller networks and devices worldwide via standardised protocols and enables data exchange across the entire globe.
1.1 How can the participants be connected?
Basically, a distinction is made between two physical connection types: Wired or wireless. In the first case, data is exchanged between the network participants via physical lines, usually copper cables or fibre optics. In wireless networks, data is transmitted via electromagnetic waves.
1.2 Which topologies can be used for connecting?
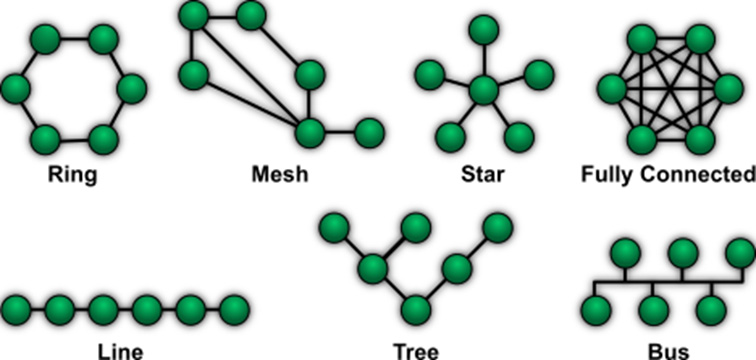
Fig. 1: Examples of possible topologies
In network technology, topology is defined as a scheme according to which the various network participants are connected. Hierarchies and transmission paths in the network depend on the topology. A device that establishes a connection between two other participants (for example, a router or switch) is called a network node. A small selection of frequently occurring topologies are presented here.
The simplest form is the point-to-point topology, where two units are directly connected. Such an example was given at the beginning of the chapter.
In small networks, a star topology is often found in which all participants are connected to a central distributor. In a home network, for example, this is the router that connects all devices – PCs, smartphones, etc. – to each other.
An extended form of the star topology is the tree topology, in which several nodes are hierarchically linked. This distributes the transmission load among several nodes. However, if one of the nodes fails, all following nodes and devices are disconnected from the network.
Larger networks are usually meshed, which means that the participants have more additional connections to each other than theoretically necessary. If a node fails, data can still be routed to its destination via the additional paths. The best-known meshed network is the Internet.
Wireless networks based on a cell topology are a special case. Here, there is a base station (in the domestic Wi-Fi, for example, the router), which receives and transmits data from the wireless network participants in a surrounding area – the cell. In wireless networks with several base stations, such as the mobile network, a device can change the associated base station (in this case the transmission mast) when it moves to another location.
2 What networks are there?
As shown at the beginning, there are too many different types of networks to explain them all in a meaningful way. In the following, we will go into more detail on a few particularly relevant types, which are distinguished by their logical spread – self-contained or publicly accessible.
2.1 What is a LAN?
The LAN (Local Area Network) is a network that is limited to a comparatively small space, such as an internal company network or the home network of a household. A LAN is a private, self-contained network that is usually connected to the Internet and thus to external networks via a router. While each participant in the LAN has a unique network or IP address, all data traffic to the outside is routed through the router, which disguises the private addresses and replaces them with its own, publicly accessible IP address. You can find out more about IP addresses in Chapter 3.2.
In the LAN, the Ethernet protocol is most commonly used for communication.

Fig. 2: The router connects the LAN to the outside world
Image by Weihao Chiu under the CC BY-SA 3.0 licence
A well-known subtype is the WLAN (Wireless LAN, typically known as Wi-Fi), in which the networking of the network participants takes place wirelessly. The basic logical structure remains the same, only the transmission medium is different. In order to avoid eavesdropping on private data, signals in the Wi-Fi are almost always transmitted in encrypted form.
2.2 What is a WAN?
In contrast to the LAN, the WAN (Wide Area Network) extends over a much larger geographical area. A WAN can connect several LANs and devices even across countries. In the WAN, each network subscriber has a unique public IP address via which it can be addressed worldwide.
Well-known WANs are, for example, the networks of Internet providers that connect home and company networks via their infrastructure and grant participants access to the Internet or other services.
2.3 What is a VPN?
In contrast to LAN and WAN, a VPN (Virtual Private Network) is a virtual network that uses existing physical networks for data transmission. In a VPN, participants typically connect to a remote network via the Internet as if they were physically present, i.e. directly wired to the LAN. The data traffic is routed via a so-called VPN tunnel, which not only verifies the device as a network participant, but also encrypts the communication and thus protects it from eavesdropping by third parties. The VPN user has full access to all resources in the LAN, such as network printers.
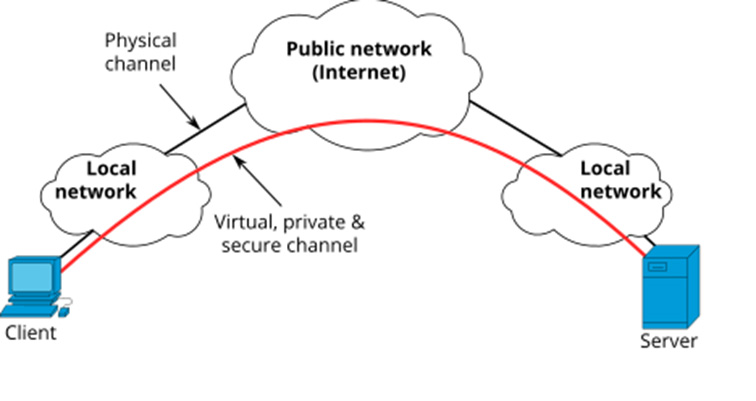
Fig. 3: Schematic representation of a VPN
Based on an illustration by Michel Bakni по CC BY-SA 4.0 licence
Nowadays, VPNs are not only used to connect to the company network in the home office. Private VPNs are often used to connect to the Internet via an external service provider and to encrypt the data traffic there. When accessing external resources via the Internet, the provider then only sees the public IP address, i.e. the network address, of the VPN provider, but not the private IP address of the actual user, which improves the anonymity of the user.
3 Which protocols are used in network technology?
In order for the different devices and structures to be able to communicate with each other, protocols are necessary that determine how the communication takes place. In a simplified way, this can be seen as a language – a vocabulary and a syntax that everyone is familiar with ensures that everyone understands each other. Each network participant must support the protocol used in order to participate in the communication. A protocol defines how the data to be transmitted is packaged, the path the packets take from the sender to the receiver and how the receiver is uniquely identified within the network.
3.1 What does TCP/IP mean?
TCP/IP is a collection of protocols that enables devices to communicate via the Internet and thus forms its technical basis. The protocols TCP (Transmission Control Protocol) and IP (Internet Protocol), which give TCP/IP its name, are crucial because they regulate the structure of data packets and their delivery. In the OSI model, these are the transport and network layers.
| 7: Application | Applications | HTTP, FTP, SMTP, DHCP |
| 6: Presentation | ||
| 5: Session | ||
| 4: Transport | Transport | TCP, UDP |
| 3: Network | Internet | IPv4, IPv6 |
| 2: Data link | Network access | Ethernet, Wi-Fi (802.11) |
| 1: Physical |
Table 1: TCP/IP protocol family in the OSI model
The control protocol (TCP) defines the structure of the data to be transmitted. Here, the data stream is divided into several numbered packets whose integrity can be verified by the receiver by means of an additionally attached checksum. As a result, the data volume with TCP is somewhat larger than with UDP, for example, but the receiver can request missing or faulty data packets again, which reliably corrects data loss and corruption.
IP controls the delivery of data packets. The sender and receiver of the packet are known via unique addresses (see 3.2). The packet can be delivered via many nodes; each path via a node is called a hop. If a transmission path fails, the Internet Protocol simply routes the packet via other nodes to the destination. Due to this decentralised transmission, the Internet continues to function even if individual components fail.
3.2 What is a network address?
The network address is a string of characters that uniquely identifies a network subscriber. The best-known formats for network addresses are based on IP.
Commonly, “IP” is understood to mean the IP address of a device. In fact, the IP address is only a network address within the entire Internet Protocol.
The most common network addresses are IPv4 addresses. These consist of a sequence of 4 bytes, each of which can have a value between 0 and 255, e.g.103.0.113.295.
Since the address range of IPv4 allows a maximum of 232 (just over 4 billion) addresses and this number will be reached worldwide in the foreseeable future due to the steady increase in Internet-capable devices, IPv6 was developed. In this version, network addresses consist of eight 4-byte segments, such as 2001:0db8:85a3:0000:0000:8a2e:0370:7344. 2128 addresses are thus possible, which is why IPv6 will replace IPv4 in the future. Modern operating systems already support IPv6.
IP addresses are divided into two categories: Public and Private IP addresses. Public IP addresses are used to precisely address the subscriber up to the router. Similar to a postal address, earlier bytes describe the rough location of the network participants, while later bytes define where exactly the participant is located in this rough area.
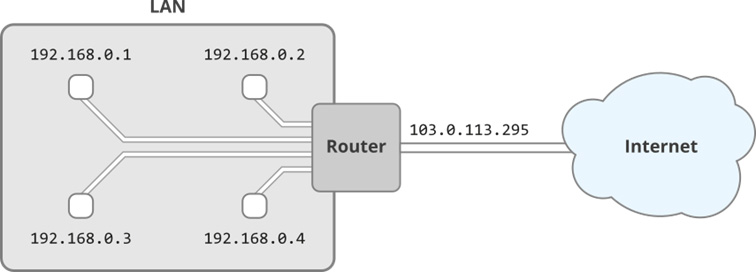
Img. 4: Public and private IP addresses. From outside, only the router’s public IP address of is visible.
Private IP addresses, on the other hand, are not publicly visible, but are assigned by the router to uniquely identify the network participant in the LAN. The public IP address of the router assigned by the ISP (Internet Service Provider) is visible to the outside world and can be used by foreign participants to communicate with the participant in the LAN. The router then translates the public IP address into the private IP address so that the data packet is delivered to the correct LAN participant. The address range for private addresses is defined via RFC 1918.
| 10.0.0.0 | 10.255.255.255 |
| 172.16.0.0 | 172.31.255.255 |
| 192.168.0.0 | 192.168.255.255 |
Table 2: Address ranges reserved for private addresses according to RFC 1918
Through the interplay of private and public IP addresses, it is possible to connect significantly more participants to the Internet than is theoretically possible, as private IP addresses only have to be unique within a LAN, but can also be assigned in other LANs. Via the public IP address, the network subscriber can be found unambiguously despite potentially identical private addresses.
Summary
Networks are created as soon as several devices exchange data with each other. They range from small direct connections to local networks to the Internet, which spans the entire globe. The structures used can take a wide variety of forms, regardless of whether copper cable, fibre optics or radio is used. Standardised protocols enable reliable data transmission.